Selectively restrict access or authorization to a enter a place or consume resources. Using an access control system at business place can increase security while managing the staff flow. Access control systems facilitate the secure management of your building.
Service
Time, Access Management Systems

Why access control systems?
Components of ACS
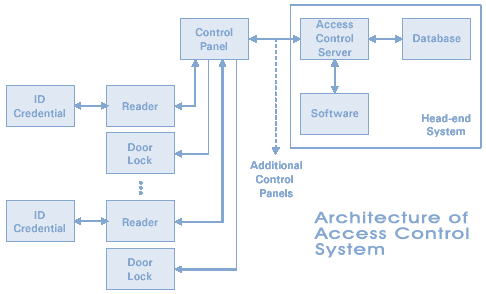
Control panel / Controller
An access-controlled entry - door/turnstile/parking gate/elevator/other physical barrier
Readers at entry / exit or both as per requirement
Locking hardware - electric door strikes/electromagnetic locks
A magnetic door switch
Request-to-exit (RTE) devices
Types of access control technologies
Various types of access control technologies used by TTFT
Access Technology Architectures
Internet of Things (IoT) access control: Enables IP-based communication between all components of the access control technology. These components which are smart devices that support IP use the Internet to establish communication with each other
Physical Access Control System (PACS): This technology used in government and security-related fields is based on Personal Information Card Verification (PIV) cards and card readers which involves a two-step verification process.
Communications Technologies
Radio Frequency Identification (RFID) access control: When approaching the reader device, electromagnetic waves are generated and captured to read information stored on a tag linked to the carrier and allow / deny access
Near Field Communication (NFC) access control: Near Field Communication(NFC) on mobile phones is expected to be a safe and effective access control solution. With NFC, users only need to wave their mobile phone at the reader to enter a lab, office, or other protected areas
Bluetooth Access Control (BAC) access control: This uses the function of a Bluetooth-enabled device by which the data transmitted between two devices through the frequency hopping spread spectrum radio interface, that operates in the ISM frequency band
Wireless access control technology: Bluetooth, NFC, RFID, mobile, and others comes under this category of access control technologies.
Authentication Technologies
Biometric access control technology: The biometric system uses fingerprints instead of a card system to access. It not only allows entry, but also provides data on staff entry. These systems can be integrated with the attendance and payroll software to automatically record the information generated by the attendance system.
Proximity card access control technology: Proximity card-based access control systems are widely used in computer rooms, businesses, financial institutions, offices, labs and factories where the employees are given access based on proximity cards. The readers which are installed at each entry and exit point can be connected to the electronic lock through the relay module. The card reader that accepts the card will disable the lock and the Configuration, Alarms, Door settings can be done using the system software. Larger buildings use integrated access control system using networking of Multiple card readers.
Mobile Access Control (MAC): By installing an application that uses wireless technology to communicate, the mobile device becomes an electronic key which can be used to control the entire access control system of a specific area/building
Two Factor Authentication in access control: This uses a combination of two distinct components to verify the authenticity of the claimed identity. 2FA is a type of multi-factor authentication which typically work with an additional layer of security, unlike single-factor authentication, which relies on passwords, improves security and makes it difficult for an attacker to break in/access sensitive data.
Palm reader: Scans the palm of a person’s hand to allow access.
Password Protection: Controls access through protected password consisting of a combination of set of letters, numbers, and symbols.
Voice Recognition: Recognizes the person’s unique voice pattern to give access
Retina Scan: Awards access by scanning and identifying a person’s eye/retina.
DNA Scan: Futuristic technology/system, requires sample of saliva or blood to check for and verify the person’s DNA
Key Card ACS: System uses a card with a magnetic/computer chip, swiped through a card reader.
Infrastructure Technologies
Internet switches for access technology
CAT6 Cable access control technology: Such ACS uses CAT6 cables to improve performance, speed and reliability.
Power over Ethernet (PoE) access control: It is a cost-effective system which uses cables to carry data/power signals across access control components such as IP cameras, telephones, access controllers, routers, access points, and other items.
IP based Access Control: It includes an electronic access controller, designed to control access to restricted areas and accurately identify users. Such a controller can support multiple access control readers that reads a person’s card number or PIN code and send it to the main server via Ethernet.

